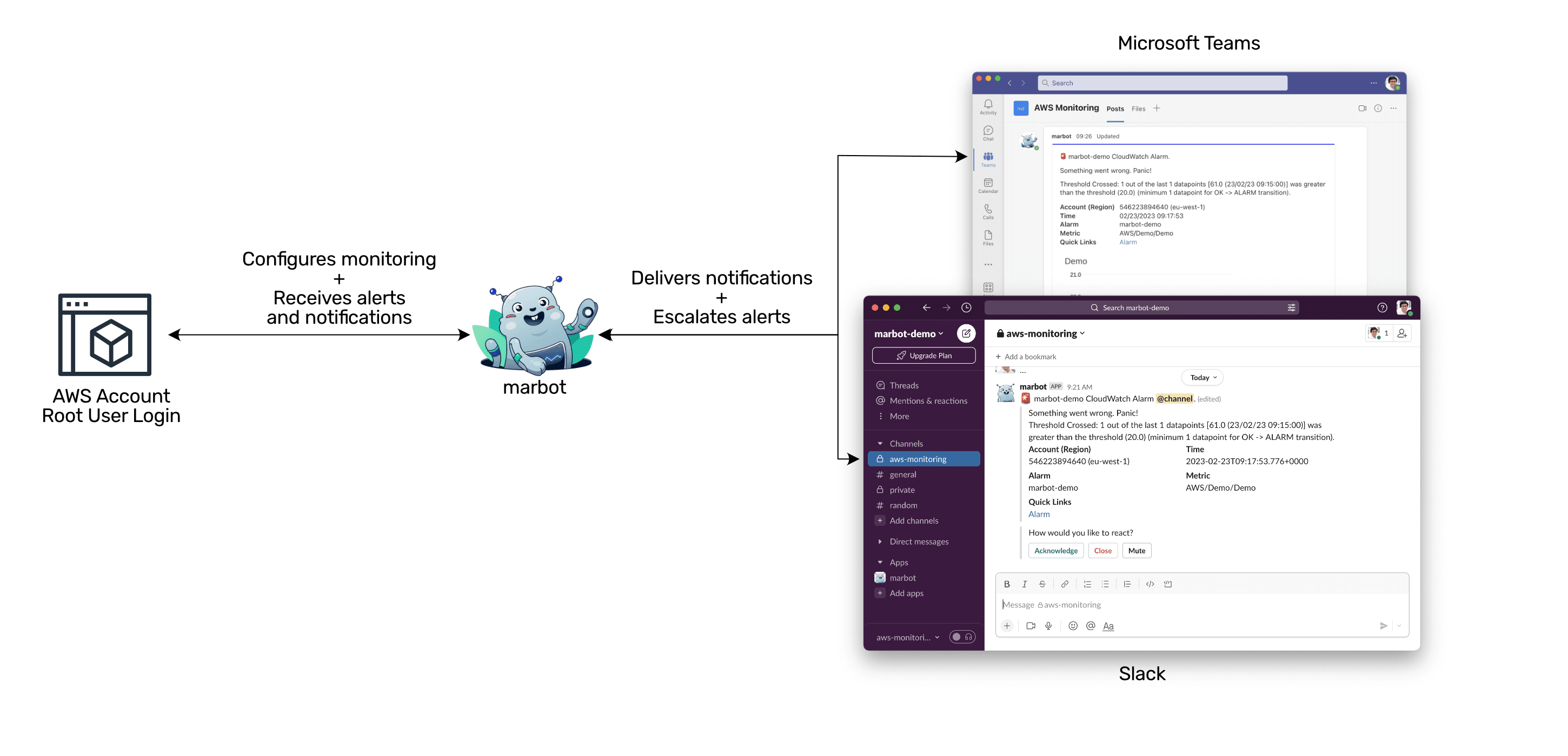
Monitoring: AWS account root user login
The AWS account root user has complete access to all AWS services and resources in an account. This identity is accessed by signing in with the email address and password used to create the account. As a best practice, we do not recommend using these credentials for everyday tasks.
Why should you monitor AWS account root user logins?
The AWS account root user should only be used in emergencies. For example, if you locked yourself out of an AWS account by a misconfigured IAM policy. In day-to-day use, the credentials for the AWS account root user should be kept in a safe place and not used. Using the AWS account root user is a security risk and should be closely monitored.
How does monitoring AWS account root user logins work?
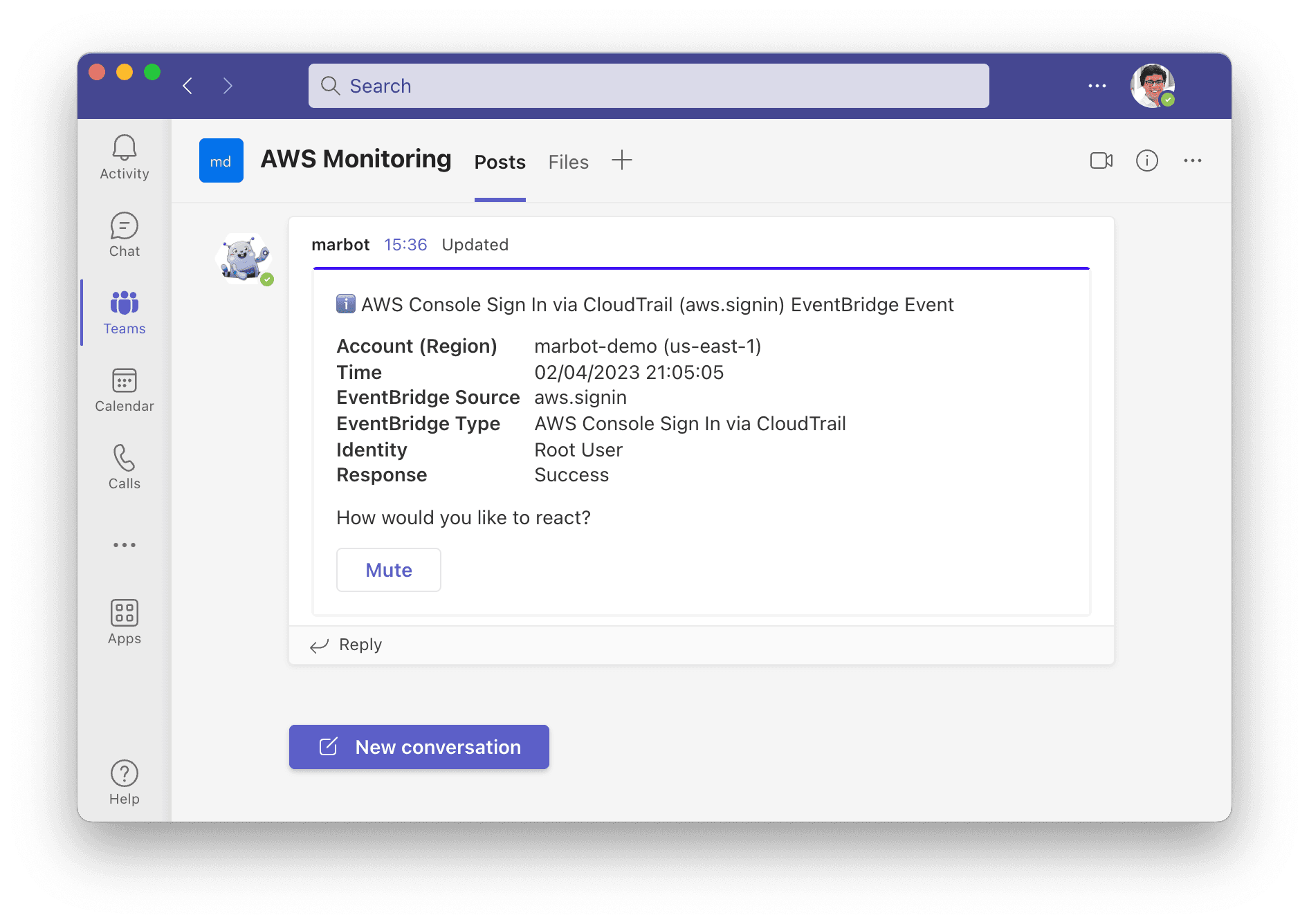
Without further ado, marbot notifies you about AWS account root user logins. Here is what an alert caused by a root user login looks like in Microsoft Teams.
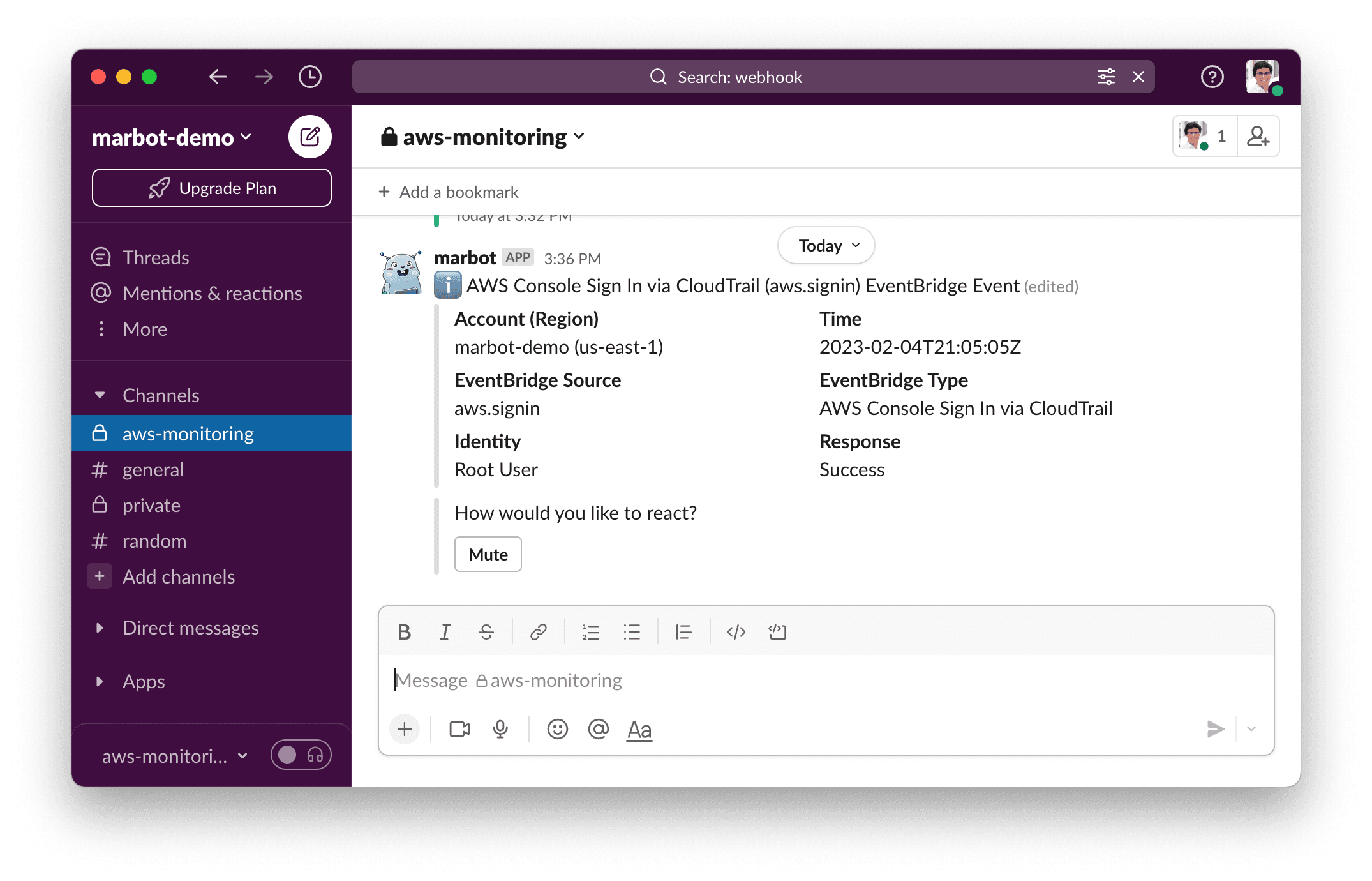
And here is the same alert in Slack.
How do you set up monitoring of AWS account root user logins?
marbot works with Slack and Microsoft Teams. Please select your platform and follow the Getting Started guide.
Which events does marbot monitor in detail?
marbot creates EventBridge rules to monitor the following events automatically.
| Event Type | Description |
|---|---|
AWS Console Sign In via CloudTrail |
Get notified if a root user signs in. |

Chatbot for AWS Monitoring
Configure monitoring for Amazon Web Services: CloudWatch, EC2, RDS, EB, Lambda, and more. Receive and manage alerts via Slack. Solve incidents as a team.