EC2 vulnerability and compliance violation alerting powered by Amazon Inspector
Michael Wittig – 25 Jan 2021
The AWS Shared Responsibility Model is clear: running EC2 instances comes with many customer responsibilities. You have to patch your EC2 instances, harden the operating system, encrypt your data, secure remote access, and many more. But how can you tell that you are not meeting your responsibilities?

In this blog post, you learn to automatically check your EC2 instances for:
- Unintended network accessibility
- Vulnerabilities
- Deviations from best practices (such as CIS Amazon Linux 2 Benchmark)
Amazon Inspector is the service of choice. Inspector relies on an agent to collect the needed information on your EC2 instances. Findings are presented in a table and include remediation hints.
As soon as a violation is detected, your team is notified in Slack or Microsoft Teams by marbot.
Let’s get started.
Please note, this blog post is about Amazon Inspector v1. In case you are using the latest version of Amazon Inspector, please proceed with Monitoring: Amazon Inspector v2 instead.
Installation
- Add marbot to Slack or Microsoft Teams.
- Invite marbot to a channel.
- Send
@marbot Create an SNS topicto the channel. - Follow the wizard in the channel.
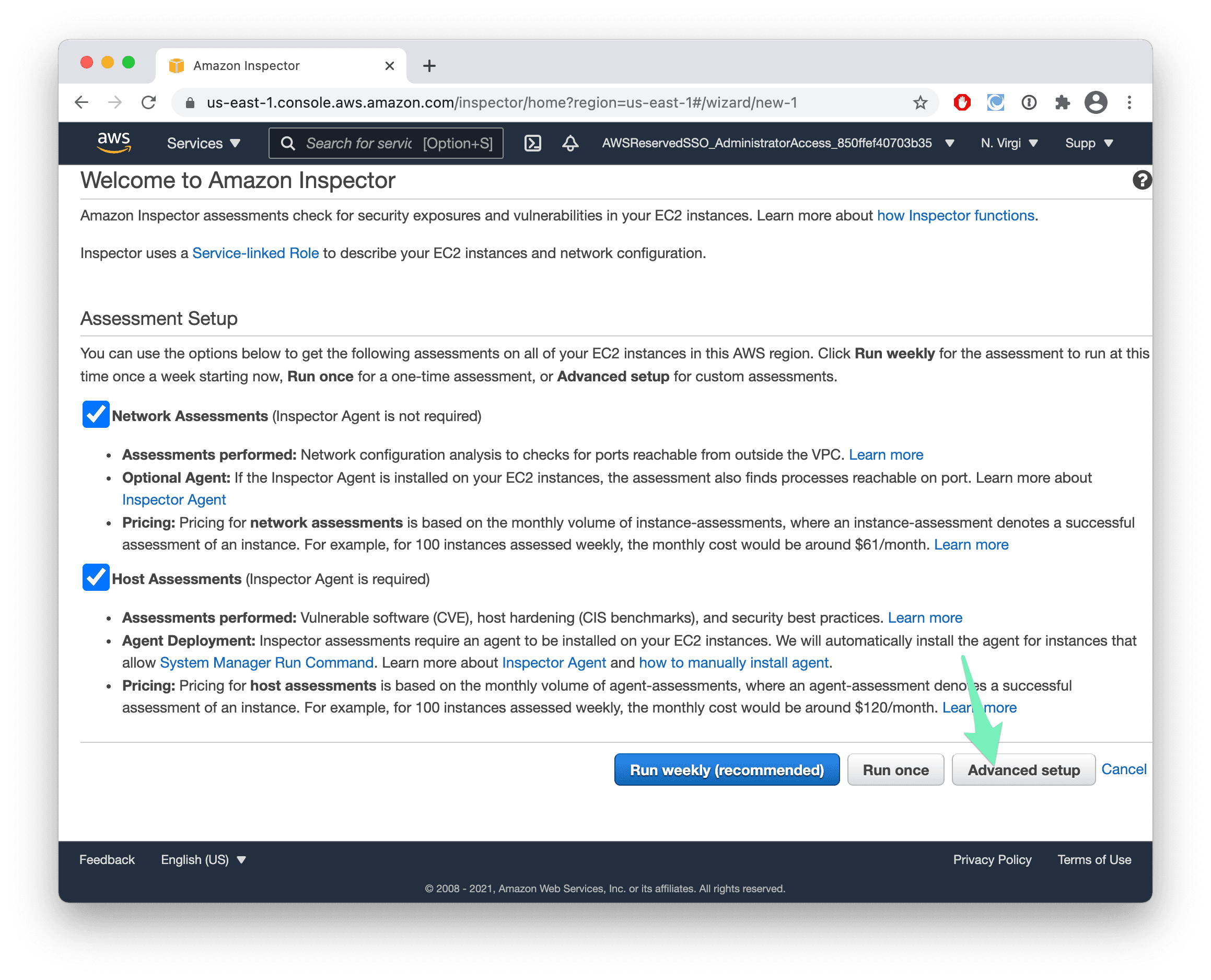
- Visit the Amazon Inspector Management Console and press the Get started button.
- Select the Advanced setup.
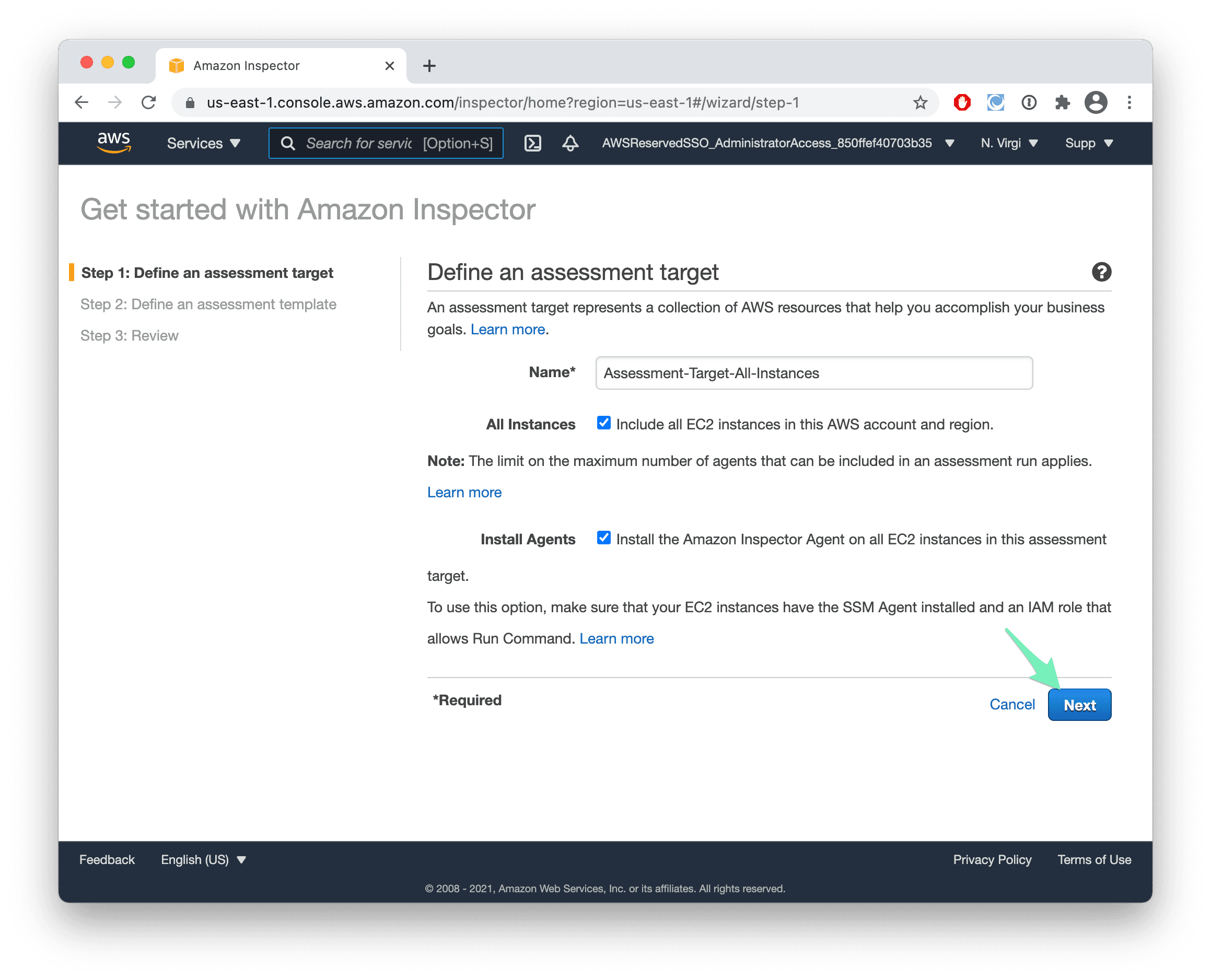
- Keep the defaults and press Next.
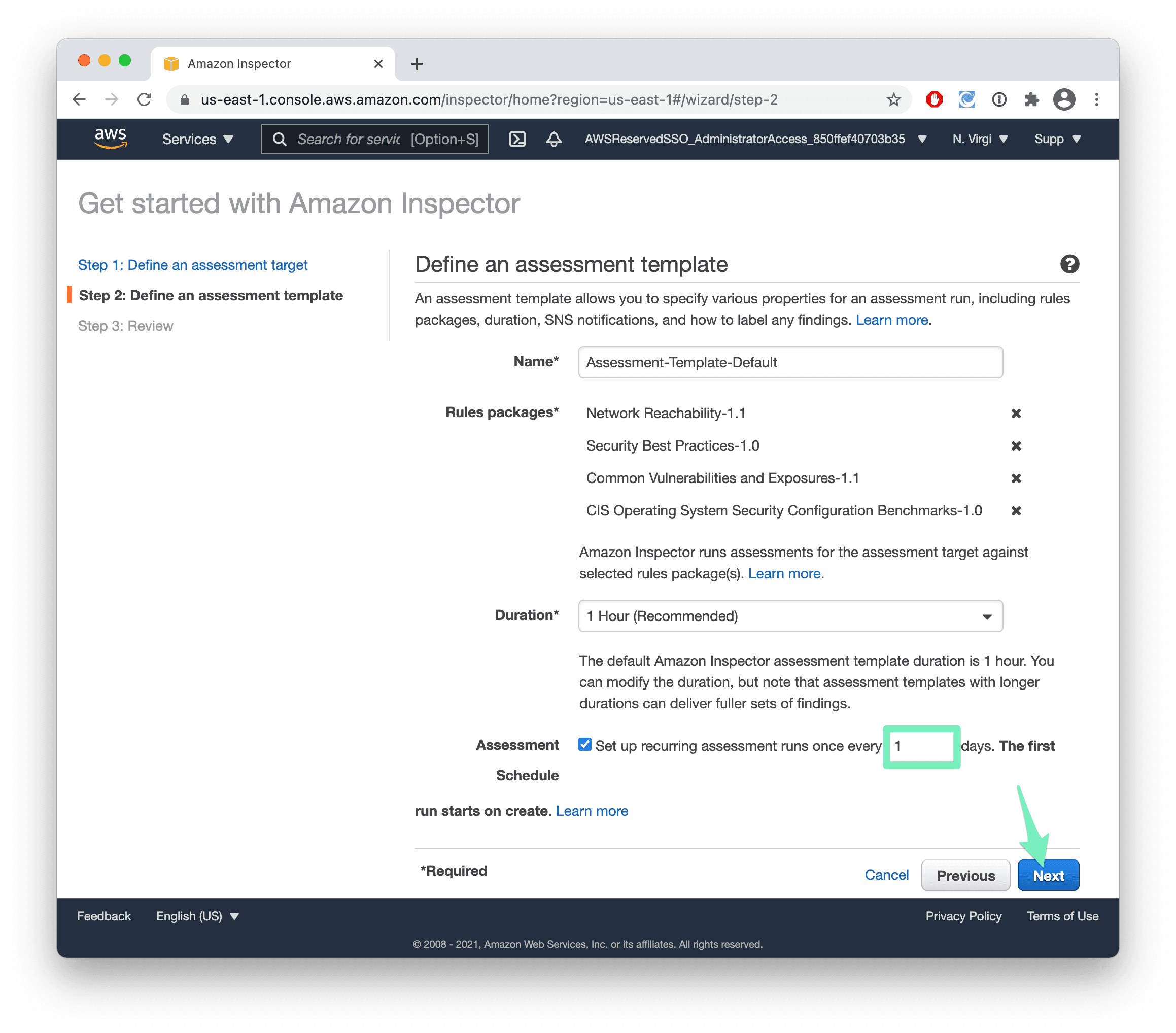
- Set the Assessment Schedule to 1 day and press Next.
- Press Create.
- Expand the assessment template Assessment-Template-Default-All-Rules and edit the SNS topics.
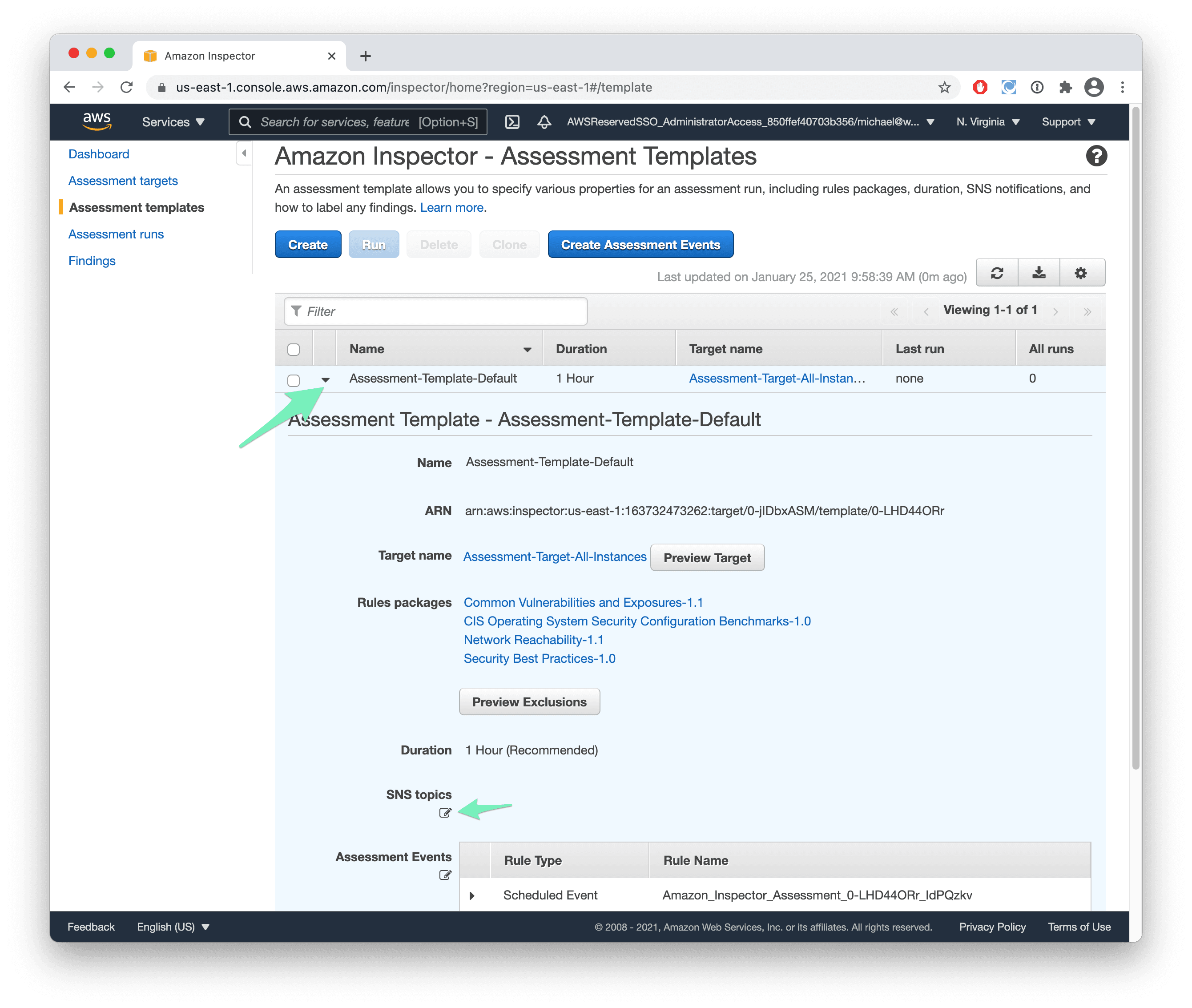
- Select the SNS topic with marbot-standalone-topic in its name and press Save.
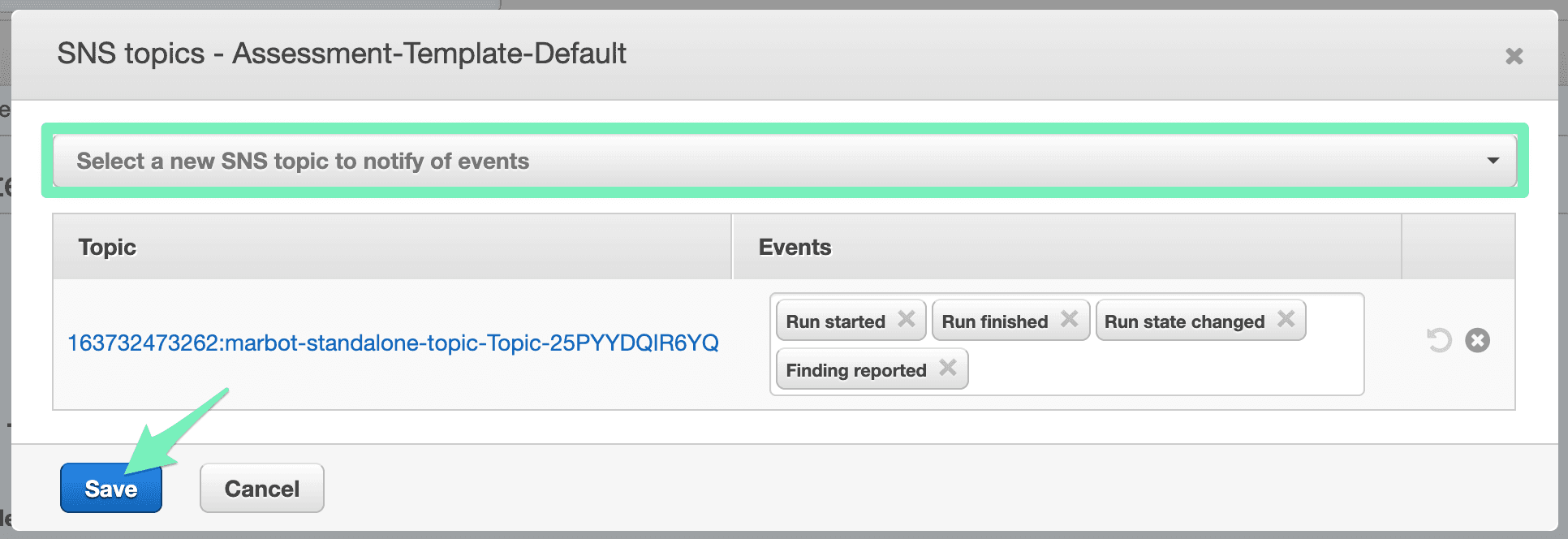
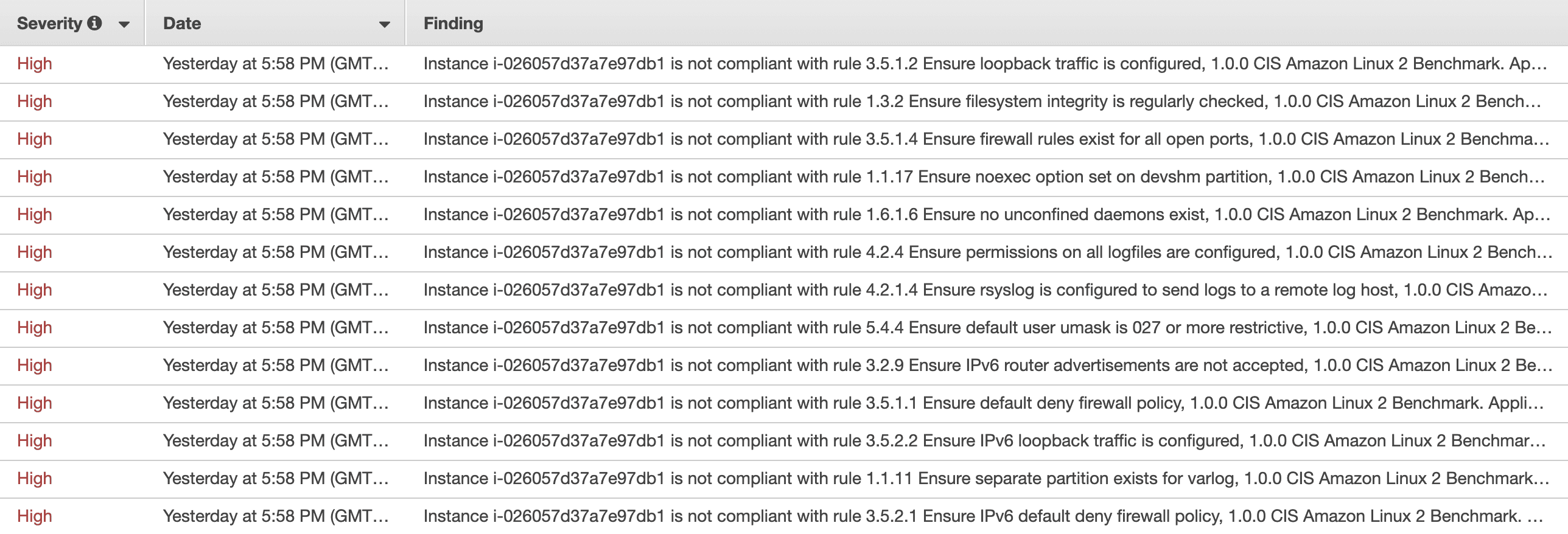
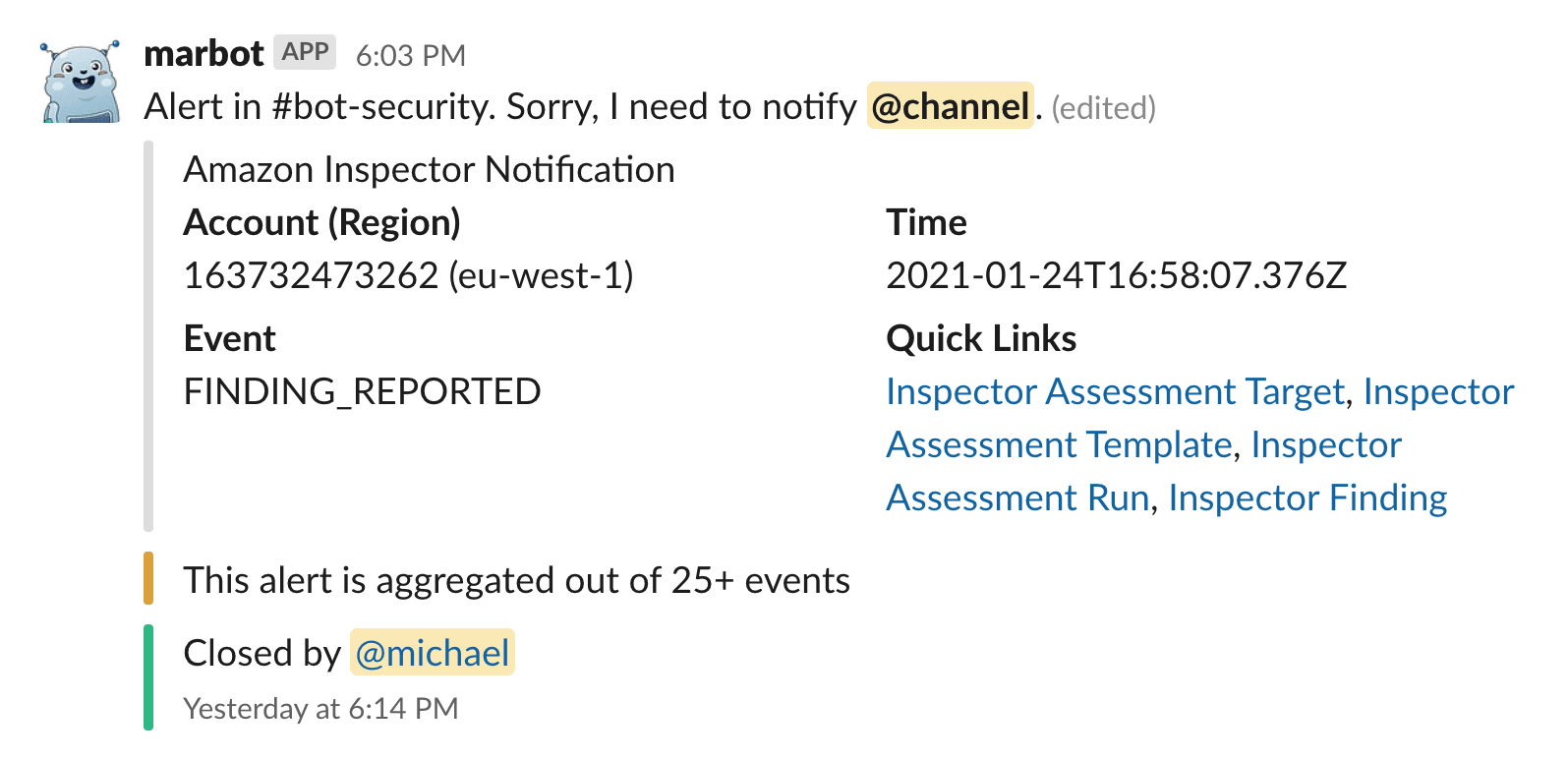
That’s it. New findings are reported to Slack or Microsoft Teams like this:
If your EC2 instances are not running the SSM agent, you have to install the Inspector agent manually.
Take your AWS monitoring to a new level! Chatbot for AWS Monitoring: Configure monitoring, escalate alerts, solve incidents.

